People want to change IP address for a variety of reasons. The Internet Protocol (IP) address is popularly known as the IP address. This private address is used by PCs for any computer network for the communication and identification processes. It is used for the identification of electronic devices connected on a network. Therefore every device is provided with a unique address.
There could be several reasons as to why you might want to change IP. Fortunately, this is something that a user can generally accomplish without any hassle
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit OK
You should now be at an MS DOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
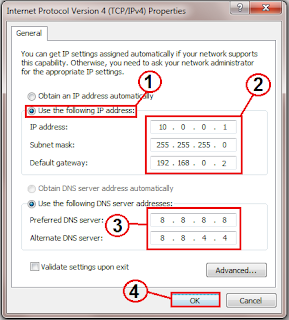
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back
There could be several reasons as to why you might want to change IP. Fortunately, this is something that a user can generally accomplish without any hassle
How to change IP Address:
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit OK
You should now be at an MS DOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here
14. Hit the "Ok" button again
You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings
17. This time, select "Obtain an IP address automatically"
tongue.gif 18. Hit "Ok"
19. Hit "Ok" again
20. You now have a new IP address
With a little practice, you can easily get this process down to 15 seconds.
P.S:
This only changes your dynamic IP address, not your ISP/IP address. If you plan on hacking a website with this trick be extremely careful, because if they try a little, they can trace it back